Protecting yourself from phishing attacks
Phishing is a form of social engineering attack that is used to steal user data such as login credentials, credit card information, or other forms of personal data. Phishing attacks are becoming more and more common, and attackers are getting far better at disguising themselves. Phishing attacks are so effective because attackers use sophisticated dupes to trick users into clicking links that then download malware or ransomware. For example, an email containing a link from a trusted person in your network—however, the person is only a guise, and the email sender is not actually in your personal network and is using a similar name or email address to that you are familiar with. The effectiveness of phishing attacks is high due to the ease of clicking malicious links. We are more likely to click links from those that we believe to know.
These attacks can also be devastating. For individuals, this can mean a loss of funds, identity theft, or unauthorized purchases. For organizations, it can mean the same but on a larger scale. Attackers can gain access to company secrets, financial information, client data, and more.
Regardless of the attack being to an individual or an organization, those on the receiving end typically sustain major financial losses, must recover from tarnished reputations, and could lose significant client-company trust. Some phishing attacks are so harmful that they can break a business beyond repair.
A popular example of a phishing attack is one that asks users to reset a password. For example, you receive an email from an address that claims your user password is about to expire and you must enter a new one to renew your account. Upon clicking the link, you will be redirected to a page that looks identical to that of the real service’s page. As you enter your old and new password, an attacker monitors your keystrokes uses your inputted password to gain access to the real service or website. These types of attacks are highly effective.
As mentioned above, phishing attacks have become more sophisticated in recent years. Now, users need to worry about regular phishing attacks—which act like a shotgun, targeting a wide-array of users at random—and spear phishing attacks—which target a very defined and researched group of individual users.
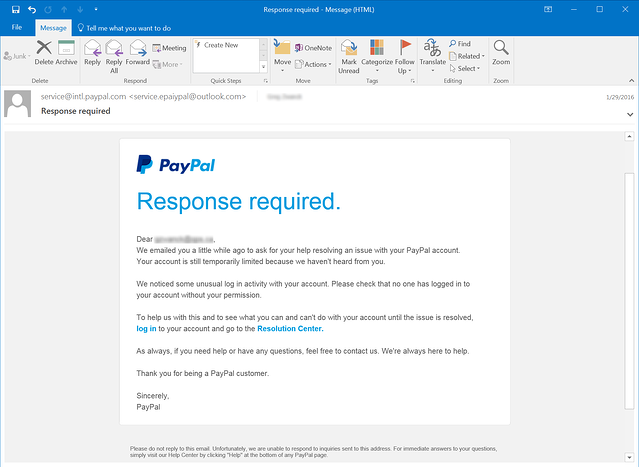
Phishing attacks are sophisticated. The image above demonstrates just how easy they are to succumb to.
Spear Phishing
Spear phishing attacks require special information or knowledge about an organization, including its power structure. They work as follows:
These types of attacks can go for weeks without anyone noticing.
Preventing Phishing
Above all, staying vigilant will protect you and your enterprise from phishing attacks. Additionally, the following can be implemented to ensure data is secure and the risks of attack are minimized.
If you or your organization require security education or monitoring, Contego can help. Simply fill in the contact form below with any questions you may have, and we will get back to you shortly. Your security should be your number one priority.






